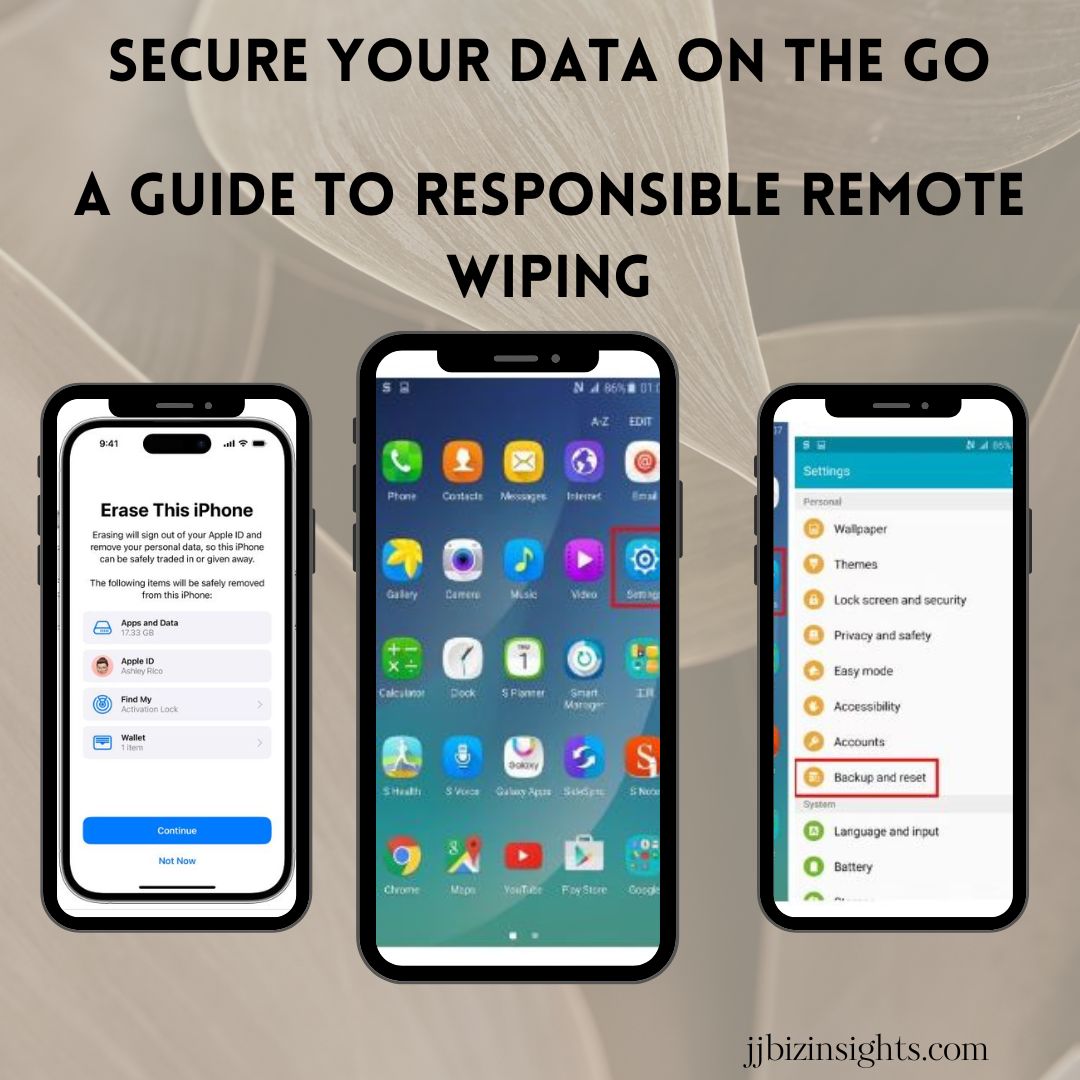
Secure Your Data on the Go: A Guide to Responsible Remote Wiping
Secure Your Data on the Go: A Guide to Responsible Remote Wiping on Mobile Devices. In today’s mobile-first world, smartphones and tablets hold a treasure trove of our personal and professional lives. From confidential client emails to cherished family photos, these devices are packed with sensitive data. But what happens if your phone falls into the wrong hands, or an employee leaves the company with its data in tow? That’s where remote wiping comes in.

Remote wiping is a vital security measure that allows you to remotely erase data from a mobile device. It’s like a digital fire extinguisher, safeguarding your information from unauthorized access in case of loss, theft, or unauthorized use. But with such power comes great responsibility. Choosing the right method and adhering to ethical best practices is crucial to ensure maximum security without compromising user trust.
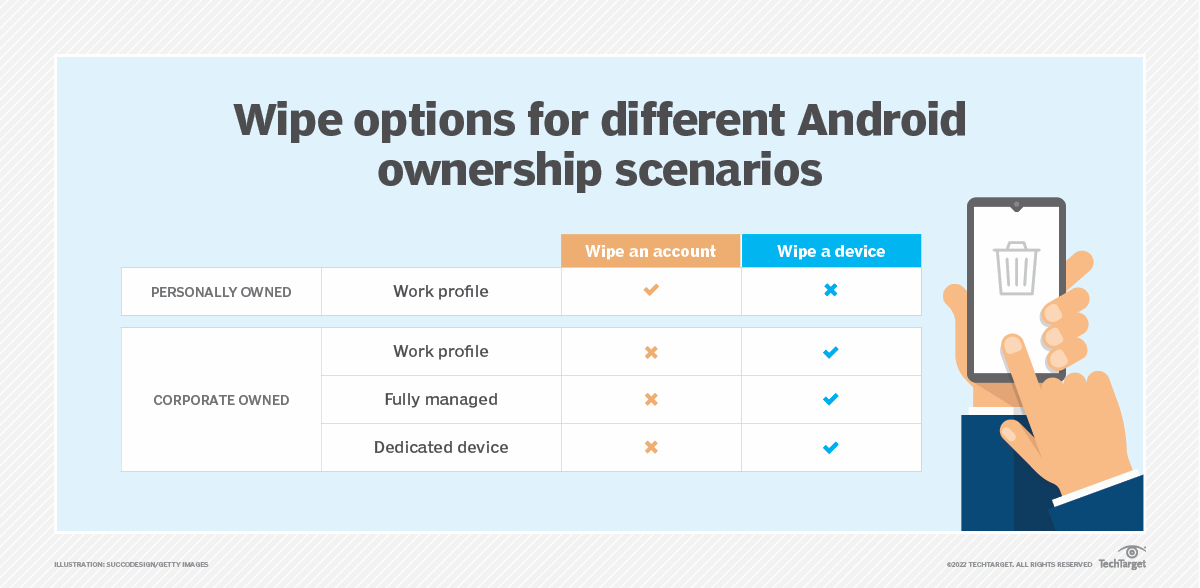
Choosing the Right Tool for the Job:
- Factory Reset: Simple and universal, but might not be effective if encryption or backups are enabled. Ideal for personal devices with minimal sensitive data.
- Device Management Software (MDM): Offers granular control over wipe scope (device or container), perfect for company-owned devices. Requires software installation and may not work on offline/powered-off devices.
- Cloud-based Services: Wipes only data stored in the cloud, leaving local storage untouched. Useful for specific data types like corporate documents.

Best Practices for Responsible Remote Wiping:
- Educate and Train: Explain the reasons for remote wipe, how to initiate it, and potential data loss implications to employees.
- Clear Policy: Outline scenarios for remote wipe, roles and responsibilities, procedures, and potential consequences. Transparency is key.
- Secure Containers: Consider utilizing containerization software to separate business and personal data, allowing selective wipes on company data.
- Backups Encourage: Regular backups of personal data minimize disruption for employees in case of a wipe.
- Test and Verify: Regularly test your chosen remote wipe method to ensure its functionality and effectiveness.
- Transparency and Communication: Inform employees about the type of remote wipe used and what data will be affected. Build trust and avoid surprises.
- Data Encryption: Enforce on-device and cloud encryption for maximum data protection. An extra layer of security for sensitive information.
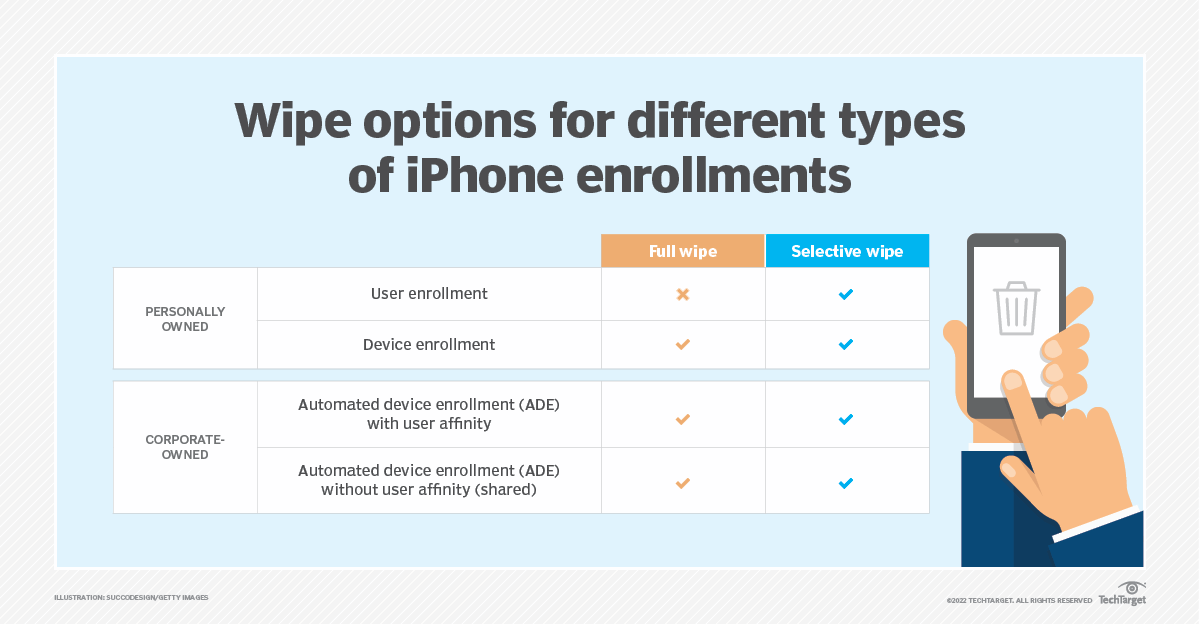
BYOD Considerations:
- Separate Data Profiles: Use containerization or work profiles to ensure only company data is wiped, leaving personal data untouched.
- Employee Consent: Gain explicit consent from employees to remotely wipe their devices as part of the BYOD agreement. Respect privacy choices.
- Clear Communication: Emphasize that only company data will be wiped and personal data remains safe. Build trust and encourage adoption of BYOD programs.
Remember: Remote wiping is a powerful tool, but it should be used as a last resort and only after careful consideration. Always prioritize data security while respecting user privacy and building trust. By following these best practices, you can ensure that remote wiping serves as a valuable safeguard for your mobile data, both personally and professionally.
For more information on remote wiping:
- TechTarget: https://www.techtarget.com/searchmobilecomputing/definition/remote-wipe
- Prey Project: https://www.techtarget.com/searchmobilecomputing/definition/remote-wipe
- Samsung Business Insights: https://learn.microsoft.com/en-us/mem/intune/remote-actions/devices-wipe
Share your thoughts: Have you ever used remote wiping? What are your concerns or experiences? Let’s start a conversation about responsible data security in the comments below!
Maximizing Security in Ecommerce Transactions





